SD-WAN Security
Ransomware attacks soar in 2016!
A new chapter on SD-WAN security?
Today applications are in the cloud; BYOD is rife, and inseparable from user-chosen operating systems; the use of cellular and broadband transport is common to augment MPLS or connect sites that MPLS cannot reach. These trends expand the attack surface of the network, while simultaneously obscuring IT visibility—evoking the adage “you cannot secure what you cannot see.”

Security breaches are on the rise.
Security breaches in the world of 2016 were abundant: the SWIFT heist in February, involving a series of banks, netted the hackers $81 million in just the first successful violation; reports of skyrocketing ransomware attacks, particularly worrisome when perpetrated against medical facilities; taxpayers finding their tax returns already filed, fueled by fraudulent access to IRS E-File PINs.
And other sobering security figures: 89% of security breaches are driven by financial or espionage; current security is not scalable and businesses are falling behind; the proverbial 50% of companies say they have been hit by malware, and the other 50% don’t yet know that they have.

SD-WAN can help.
Enter the Cloud-Delivered SD-WAN—its robust architecture uniquely flexible to secure both traffic and data, deployed as a secure overlay to a transport/provider-independent infrastructure. With several different deployment architectures, a Cloud-Delivered SD-WAN accommodates the needs of even the most security sensitive business. It also returns to corporate IT the security, compliance and control it needs to be safe.
A Cloud-Delivered SD-WAN enables unprecedented visibility into the use of datacenter or SaaS applications, applies network-wide business and security policies, inserts local and third-party security services wherever and whenever they are needed, and extends the WAN perimeter from the cloud to the branch.
Deployment Models
It is evident in the industry that the WAN architecture of a retail, health or financial institution can differ profoundly from that of a hospitality enterprise or a UCaaS provider, and again from those needed by service provider networks. The singular flexibility of a Cloud-Delivered SD-WAN allows the solution components — the SD-WAN node (single and multi-tenant for on-premises and cloud), SD-WAN Orchestrator (VCO), SD-WAN Controller (VCC) — to be deployed in multiple different architectures, including:
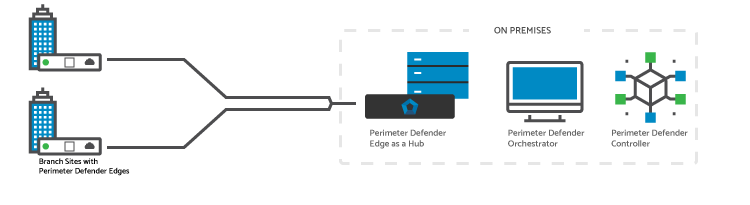
All On-Premises
This architecture, where all components of the WAN are located on premises, addresses the needs of networks that have not yet migrated to the cloud and prefer traffic to flow to the datacenter.
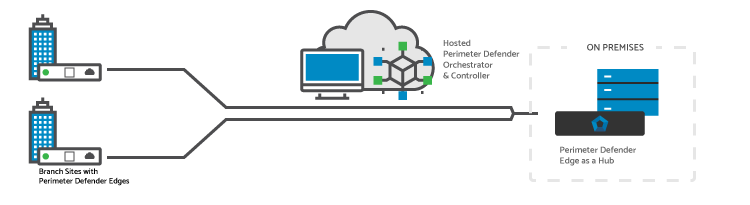
Hosted Perimeter Defender Orchestrator/Controller
Management and control (provisioning, configuration) is Cloud-Delivered, while data continues to flow on-premises between SD-WAN nodes that remain on-premises.
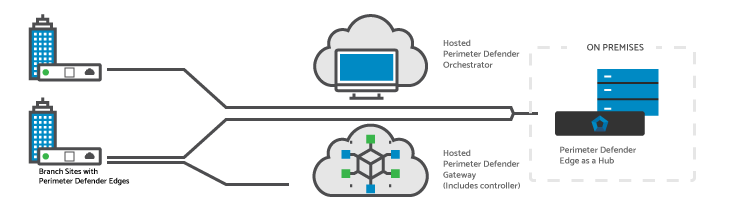
Hosted Perimeter Defender Orchestrator/Gateway
Management and control (provisioning, configuration) is Cloud-Delivered and Cloud Saas/IaaS traffic is directed to the Cloud SD-WAN node (VCG), while datacenter traffic continues to flow directly to the datacenter node.
Security, simplified.
The often vexing complexity of VPN tunnels and PKI infrastructure management in traditional WAN architectures is dramatically simplified by leveraging the secure and scalable cloud-based SD-WAN PKI infrastructure, which can be turned on with a single click on the orchestrator. VPN tunnels are built where and when needed, and covers branch-to-branch, branch-to-DC and any-location-to-cloud traffic patterns.
Pivotal security features required by a headless SD-WAN, or to secure cloud-destined traffic without hairpinning it through the datacenter, can leverage hosted security facilities, both for VPN termination, as well as for insertion of other services including firewalling and cloud-based-security (such as Zscaler). The VNF capabilities supported on the VeloCloud Edge additionally allows security service insertion in the branch.
The Cloud-Delivered SD-WAN provides CISO and CIO peace of mind that your network traffic is secure, and that your brand, customers, and employees are protected appropriately—all in an architecture that fits your unique business irrespective of whether the needs are on premises-centric, cloud-centric or a combination of these.

